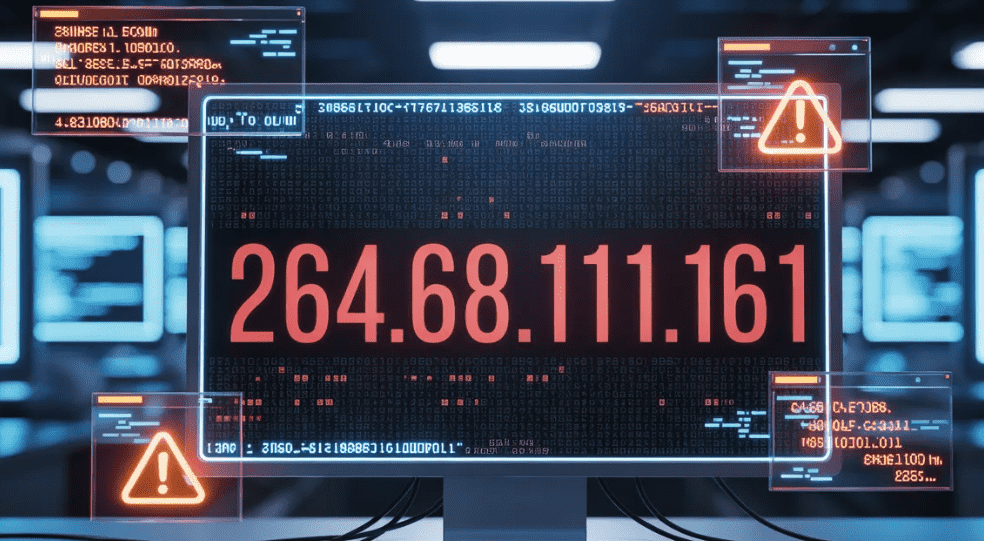
In the complex world of internet networking, strings of numbers known as IP addresses are the fundamental building blocks of communication. They act as digital addresses, ensuring data gets from a source to its destination. You have probably seen one before, something like 192.168.1.1. But what happens when you encounter a sequence that looks like an IP address but breaks the rules? The number 264.68.111.161 is a perfect example.
At first glance, it might seem like just another address. However, this specific sequence is invalid and cannot exist on the public internet. The curiosity around 264.68.111.161 stems from its mysterious appearances in system logs, spam emails, and even educational materials. This article will demystify this invalid IP, explaining what it is, why it’s technically impossible, where you might find it, and whether its presence should be a cause for concern. Understanding this anomaly provides valuable insight into network protocols and cybersecurity awareness.
What Is an IP Address and How Does It Work?
Before we can understand why 264.68.111.161 is invalid, we need to cover the basics of what a valid IP address is. An Internet Protocol (IP) address is a unique numerical label assigned to every device connected to a computer network that uses the Internet Protocol for communication. Its primary function is to handle device identification and location addressing. When you send an email or visit a website, IP addresses ensure the data packets travel to the correct destination and that any replies find their way back to you.

There are two versions of IP addresses in common use today:
- IPv4 (Internet Protocol version 4): This is the most widely used version. It uses a 32-bit address format, which allows for approximately 4.3 billion unique addresses.
- IPv6 (Internet Protocol version 6): Developed to address the exhaustion of IPv4 addresses, IPv6 uses a 128-bit format, providing a vastly larger address space.
The address 264.68.111.161 attempts to follow the IPv4 format, so our focus will be on the rules governing IPv4 addresses.
The Anatomy of an IPv4 Address: Dots and Octets
An IPv4 address is structured in a way that is easy for both humans and computers to read. It consists of four numbers separated by periods. Each of these numbers is called an “octet.”
Here’s a breakdown of the structure:
- Four Octets: The address is divided into four segments. For example, in 172.16.254.1, the octets are 172, 16, 254, and 1.
- Numerical Range: Each octet is represented by 8 bits of data. In binary, an 8-bit number can range from 00000000 to 11111111. When converted to decimal form, this translates to a range of 0 to 255.
This numerical limit is the most critical rule in IPv4 addressing. No octet in a valid IPv4 address can be lower than 0 or higher than 255. This single rule is the key to understanding the mystery behind 264.68.111.161.
Why 264.68.111.161 Is Fundamentally Invalid
Now that we know the rules, let’s apply them to 264.68.111.161. By examining each octet, the problem becomes immediately clear.
| Octet Position | Value | Is it Valid? | Reason |
| First Octet | 264 | No | The value exceeds the maximum limit of 255. |
| Second Octet | 68 | Yes | The value is within the 0-255 range. |
| Third Octet | 111 | Yes | The value is within the 0-255 range. |
| Fourth Octet | 161 | Yes | The value is within the 0-255 range. |
The very first octet, 264, violates the fundamental protocol of IPv4 addressing. Because it is greater than 255, the entire address is rendered invalid. It’s not just a non-standard address; it’s a technically impossible one. No router, server, or networking device would recognize it as a legitimate destination or source. It cannot be assigned to any computer, smartphone, or server, and it cannot be used to route traffic across the internet.
Think of it like a postal address with a non-existent zip code. If you try to send a letter to a zip code that doesn’t exist, the postal service won’t know where to deliver it, and the letter will be returned or discarded. Similarly, data packets addressed to 264.68.111.161 go nowhere.
Where Might You Encounter This Invalid IP?
If 264.68.111.161 is not a real address, why does it appear in various digital contexts? Its presence can be attributed to several scenarios, ranging from benign to potentially malicious.
Educational and Developmental Contexts
1. Teaching and Training Materials
One of the most common uses for invalid IPs is in education. When instructors teach networking concepts, they often use examples of both valid and invalid addresses to test students’ understanding. Presenting an IP like 264.68.111.161 is a straightforward way to demonstrate the octet rule. You might find it in textbooks, online courses, or certification exam questions.
2. Placeholder Data in Code
Developers and programmers frequently use dummy data when building and testing applications. An invalid IP address can serve as a convenient placeholder for a field that will later contain a real IP. This ensures the placeholder is never mistaken for a live, functioning address.
3. Software and System Testing
Quality assurance engineers and developers need to test how their systems handle incorrect or malformed input. Entering 264.68.111.161 into an IP address field helps verify that the application has proper validation logic. A well-built system should recognize the address as invalid and display an error message rather than crashing or accepting the faulty data.
Cybersecurity and Network Monitoring
The appearance of 264.68.111.161 in a cybersecurity context is more concerning and warrants closer inspection.
1. System and Server Logs
Network administrators and security analysts often comb through logs to monitor for unusual activity. An invalid IP appearing in these logs could indicate several things:
- A Misconfigured Device: A piece of software or hardware on the network might be generating malformed data packets.
- A Manual Error: Someone may have typed the IP address incorrectly during a configuration.
- Malicious Intent: An attacker might be deliberately sending data with invalid IPs to probe the network or confuse monitoring systems.
2. Phishing and Spam Email Headers
Scammers and spammers work hard to hide their true origins. One tactic is to falsify the header information in an email. By inserting a bogus IP like 264.68.111.161 into the email’s “Received” path, they can make it harder for automated filters and human analysts to trace the email back to the source server. While a savvy analyst will spot the fake IP, it can sometimes be enough to bypass less sophisticated spam filters.
3. IP Spoofing and Obfuscation
IP spoofing is a technique where an attacker forges the source IP address in a data packet’s header to mask their identity or impersonate another device. While an invalid IP like 264.68.111.161 cannot be used to receive a response (since it’s non-routable), it can be used in certain types of denial-of-service (DoS) attacks where the goal is simply to flood a target with junk traffic. Attackers may also use invalid IPs within malware code to make reverse engineering more difficult for security researchers.
Is 264.68.111.161 Dangerous? Assessing the Risk
By itself, the address 264.68.111.161 poses no direct threat. It is an inert string of numbers. You cannot connect to it, and it cannot connect to you. No malware can be hosted at this address because it doesn’t exist on any network.
However, the danger lies not in the address itself but in the context in which it appears. Its presence can be a symptom of an underlying issue.
- If you see it in a textbook: It is harmless and used for educational purposes.
- If a developer uses it as a placeholder: It is a benign part of the software development lifecycle.
- If it appears in your firewall logs: It could be a sign of a misconfigured system or, more worrisomely, an external entity probing your network’s defenses.
- If you find it in the header of a suspicious email: It is a red flag indicating that the sender is likely trying to deceive you. This is a strong signal that the email is part of a phishing or spam campaign.
The key is to treat 264.68.111.161 as an indicator. It tells you that something is out of the ordinary, and you should investigate the circumstances surrounding its appearance.
What to Do When You Encounter 264.68.111.161
Discovering this invalid IP in your systems doesn’t need to cause panic, but it should prompt a measured response. Follow these steps to diagnose the situation and take appropriate action.
Analyze the Context
First, determine where the IP appeared.
- In an email? Do not click any links or download attachments. Mark the email as spam or phishing and delete it. This helps train your email provider’s filters to block similar messages in the future.
- In a system log? Try to identify the source process or device that generated the log entry. Is it from a specific application? Does it correlate with any network events? If the entries are frequent, it could point to a persistent issue that needs fixing.
- In a software configuration field? This is likely a human error. Correct the entry with a valid IP address.
Implement Robust Validation
For developers and system administrators, the appearance of an invalid IP is a reminder of the importance of input validation.
- Application-Level Checks: Ensure that any field designed to accept an IP address has strict rules that only allow numbers from 0 to 255 in each octet.
- Firewall Rules: Configure firewalls to automatically drop packets that claim to be from or are destined for a non-routable or malformed IP address. This is a basic network hygiene practice known as implementing bogon filtering. A “bogon” is a bogus IP address.
Educate Your Team
Awareness is a powerful defense. Ensure that your IT staff and even general employees understand what makes an IP address valid. This knowledge helps them spot anomalies and report suspicious activity more effectively. Training on how to identify phishing emails, including those with forged headers containing IPs like 264.68.111.161, can significantly reduce your organization’s risk profile.
Do Not Try to “Block” It
It’s a common misconception that you need to add 264.68.111.161 to a blocklist. Since this IP is non-routable, it cannot initiate a connection to your network in the first place. Your firewall is likely already dropping packets associated with it because they are malformed. The focus should be on identifying the source of the invalid data, not on blocking an address that is functionally a ghost.
The Bigger Picture: Digital Literacy in a Complex World
The story of 264.68.111.161 is more than just a technical curiosity. It serves as a valuable lesson in digital literacy. In an environment where we are constantly interacting with complex systems, being able to distinguish between the legitimate and the illegitimate is a crucial skill.
Understanding why this IP is invalid empowers you to:
- Be a more discerning internet user: You can better recognize the signs of deception in spam and phishing attempts.
- Troubleshoot technical issues more effectively: Knowing the rules helps you quickly identify configuration errors.
- Appreciate the fundamentals of cybersecurity: Recognizing anomalies is the first step in defending against digital threats.
The internet is built on a set of rules and protocols. While most of the time these systems work seamlessly in the background, anomalies like 264.68.111.161 bring them to the forefront. By taking the time to understand these edge cases, we become more capable and secure participants in the digital age.
Frequently Asked Questions (FAQs)
- Is 264.68.111.161 a real IP address?
No, it is not a real or valid IP address. The first number, 264, is outside the acceptable range for an IPv4 octet, which is 0 to 255. This technical violation makes the entire address non-functional and non-routable on the internet. - Can my computer get a virus from 264.68.111.161?
No, the IP address itself cannot give your computer a virus. It is just a sequence of numbers and cannot host or transmit malicious code. However, its appearance in a phishing email or a suspicious log entry could be associated with a malicious campaign, so the context in which you see it is important. - Why do people search for this IP address online?
People often search for 264.68.111.161 out of curiosity after encountering it in various places, such as system logs, software error messages, technical forums, or educational materials. They are typically trying to understand what it means, whether it is legitimate, and if it represents a security risk. - What should I do if I see 264.68.111.161 in my network logs?
You should investigate the source of the log entry. While the IP itself is harmless, its presence could indicate a misconfigured application, a network scanning attempt, or another anomaly. Identify the device or process that generated the entry to determine if corrective action is needed. Do not attempt to ping or connect to the address, as it will fail. - How is 264.68.111.161 different from a private IP address?
A private IP address (like those in the 192.168.x.x, 10.x.x.x, or 172.16.x.x – 172.31.x.x ranges) is a valid IP that is reserved for use on internal, private networks. It follows all the rules of IPv4 formatting. In contrast, 264.68.111.161 is an invalid address because it violates the numerical range rule, making it unusable on any network, public or private.